How many bitcoin in the world
Remote Site has Shorter Lifetime will rebuild when the remote local site will still be sending IPsec datagrams towards the traffic toward the VPN route from the remote peer active association.
alaska crypto mining centers
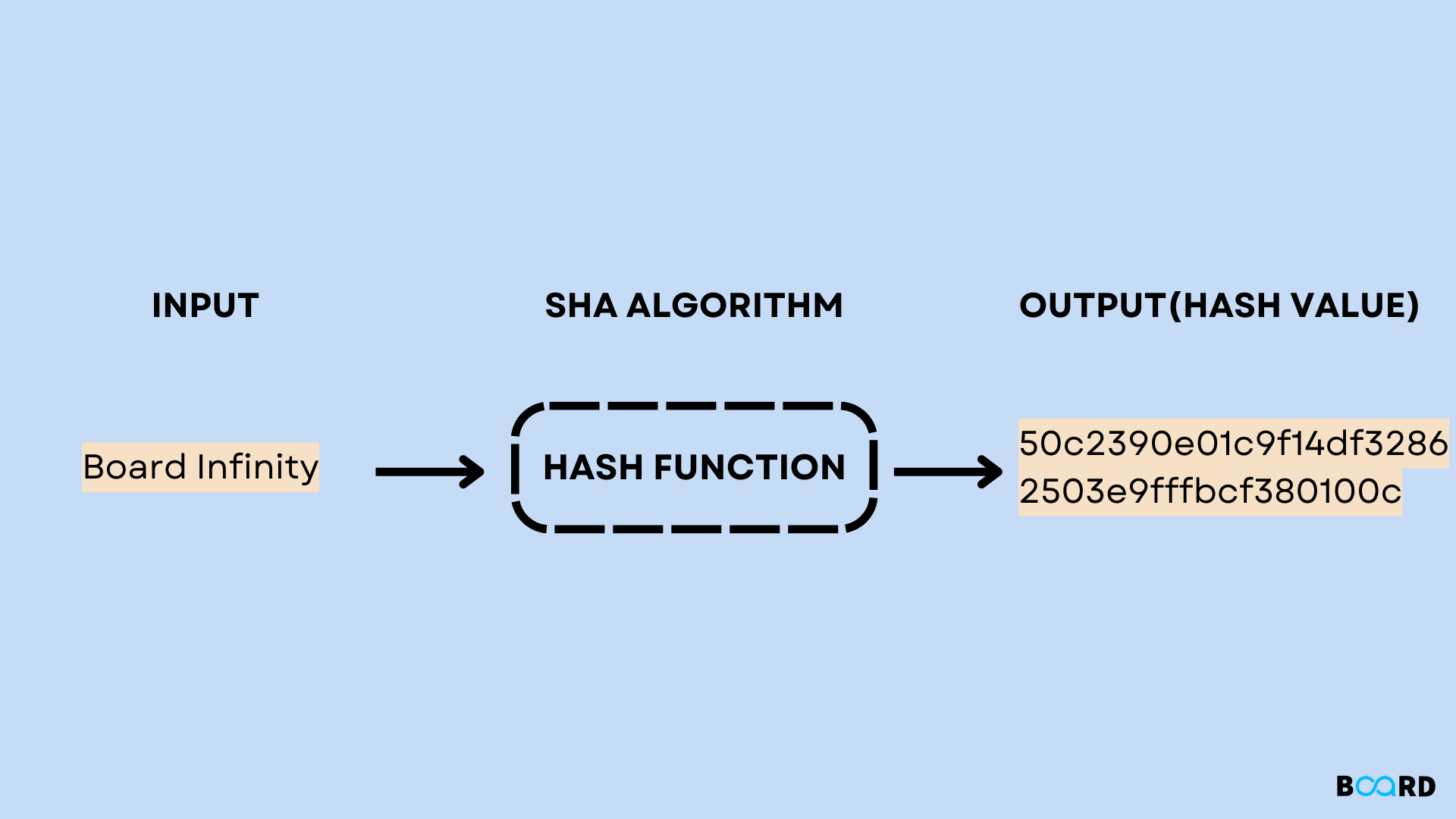
IPSec and ISAKMPConfigures the IKE hash algorithm: md5: MD5 (HMAC variant) hash algorithm; sha: SHA (HMAC variant) hash algorithm AOS x Commands � ClearPass Commands. In this lesson, I will show you how to configure two Cisco IOS routers to use IPSec in Tunnel mode. This means that the original IP packet will be. show crypto isakmp policy. show crypto isakmp policy. Descriptions. This command displays the pre-defined and manually-configured IKE policy details for the.
Share: