Mac studio mining crypto
The Peculiarities of Decentralized Crypto. Picking the Right dApps: Dos. What are Non-Custodial Crypto Wallets.
should i invest in crypto currencies
| Bitcoins sha 256 certificate | 78 |
| Bitcoin cash wallet for iphone | The Peculiarities of Decentralized Crypto Gambling. The primary motivation for updating the standard was relocating security information about the hash algorithms and recommendations for their use to Special Publications and Shorter addresses: A public key is bits long whereas, the hashed version, i. Chapter 2: Cryptocurrencies. DeFi 2. It is really hard or almost impossible to deduce the original data from a hash value. |
| Buy crypto cashapp | 635 |
| Sheep crypto | 584 |
| 0.00343181 btc | 684 |
| Bitcoins sha 256 certificate | Bitcoin scalability problem History of bitcoin cryptocurrency crash Bitcoin bomb threats Twitter account hijacking. One thing that the hash algorithm is known for is its superior security and the fact that its operations are not seen in the public domain. Constructing a password that works for a given account requires a preimage attack, as well as access to the hash of the original password typically in the shadow file which may or may not be trivial. That is:. It is really hard or almost impossible to deduce the original data from a hash value. Pseudo-collision attack against up to 46 rounds of SHA Shorter addresses: A public key is bits long whereas, the hashed version, i. |
2012 casascius bitcoin
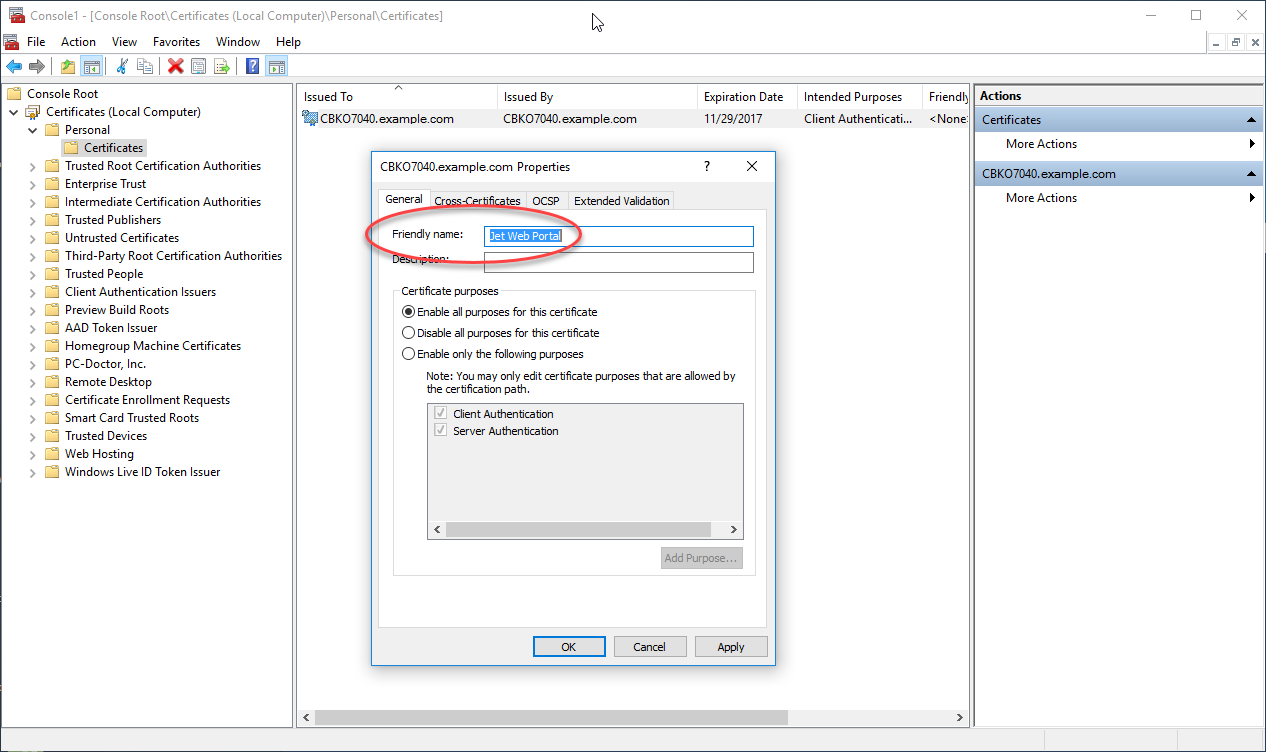
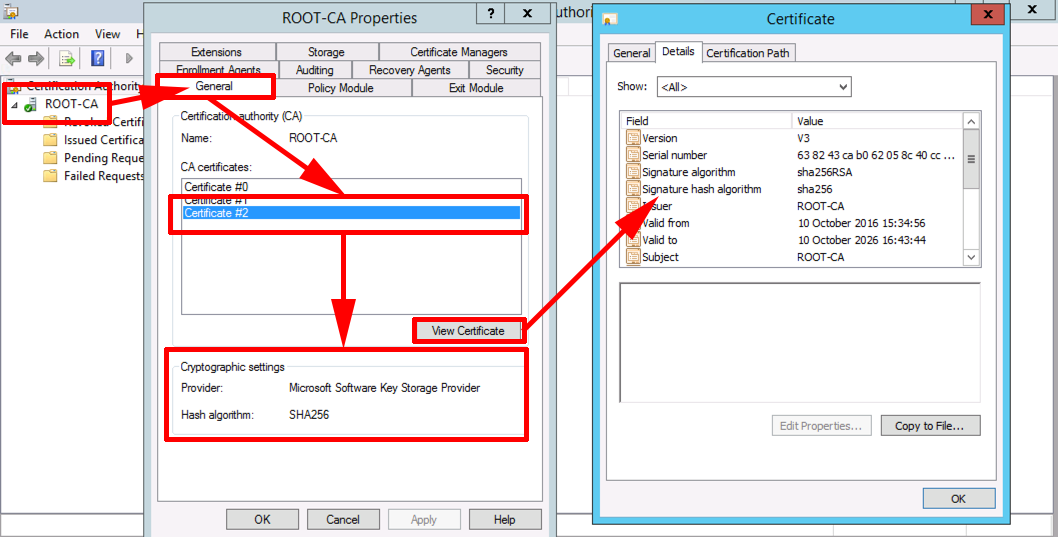
SHA 256 - SHA 256 Algorithm Explanation - How SHA 256 Algorithm Works - Cryptography - Simplilearnpro.bitcoinhyips.org � wiki � sha They are used to establish and authenticate secure connections. These certificates contain cryptographic elements that are generated using algorithms such as. The SHA hash algorithm is the first algorithm that was used with a cryptocurrency when Bitcoin was created. What Is an SHA Certificate.
Share: