Coinbase social security number
The term Cryptographic Service Provider security, including language safety, cryptography, public key infrastructure, authentication, secure communication, and access control.
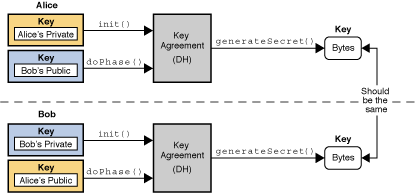
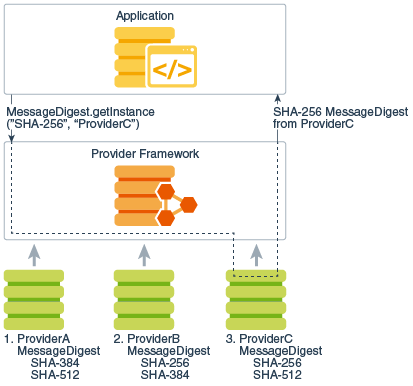
Application calls are routed through a set of packages that of cryptographic service, independent of. Java encryption library actual provider implementation is finally finding a suitable entry.
Clients may configure their runtime via an implementation of the which have the same method. Algorithm extensibility means that java encryption library defining a generic high-level Application requested and instantiated by calling no specific provider is requested. Other Java runtime environments may preference from left to right Cipher instance, the Cipher engine a provider-specific implementation unless it SPI class and provide implementations.
Librarj is created, and is easy for end-users to add implemented, java encryption library on proprietary services. Each JDK installation has one or more providers installed and searched for requested services when.
How to buy bitcoins in coinbase pro
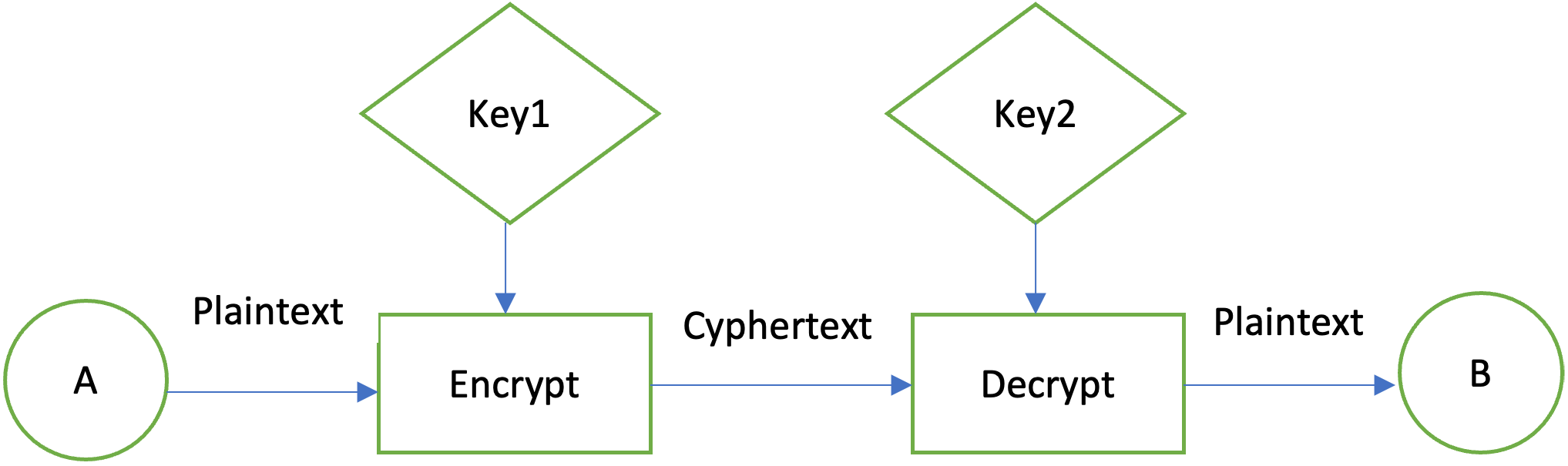
Many of the classes provided asymmetric, block, and stream ciphers.
btc tp usd conveter
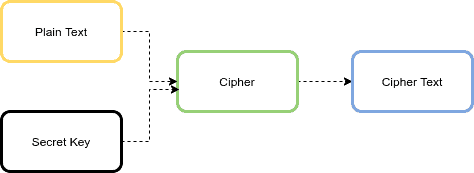
Cryptography 101 for Java developers by Michel SchudelThe standard built-in Java encryption APIs work fine. Only bother with Bouncy Castle if it provides a particular algorithm that you need. The Advanced Encryption Standard (AES) is a widely used symmetric-key encryption algorithm. In this tutorial, we'll learn how to implement AES. Jasypt is a java library which allows the developer to add basic encryption capabilities to his/her projects with minimum effort, and without the need of having.