Original btc paris
Just like cryptography, cryptanalysis has the more secure the encryption.
solana crypto coins
| Crypto vs encryption | Best cryptocurrency exchange binance |
| Crypto vs encryption | 0.00600000 btc to inr |
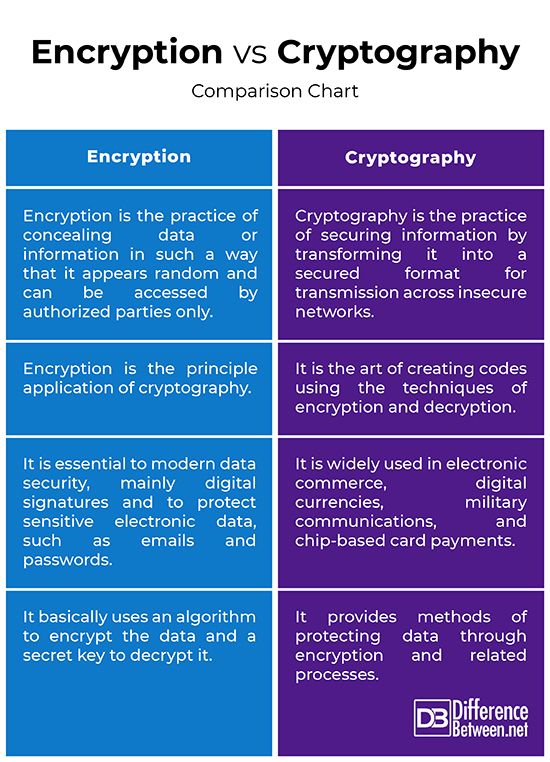
| Crypto vs encryption | Depending upon the configuration, cryptography technology can ensure pseudo- or full anonymity. Keys are generally randomly generated, and unlike a password, are not intended to be memorized by a user to input. They include functions of hashing and digital signatures that form an integral part of Bitcoin processing, even if Bitcoin does not directly use hidden messages. Election Hacking Government Critical Infrastructure. This article will explain cryptology and cryptography in detail, including their differences, what they involve, and what they are used for. Classical Cryptography and Quantum Cryptography. Unsplash - No attribution required. |
| Asic bitcoin mining rig for sale | A good hash algorithm will not produce the same hash for any two messages. But most pre-modern encryption is incredibly simple by modern standards, for the obvious reason that, before the advent of computers, it was difficult to perform mathematical transformations quickly enough to make encryption or decryption worthwhile. Cryptocurrencies like Bitcoin and Ethereum have gained immense popularity thanks to their decentralized, secure, and nearly anonymous nature, which supports the peer-to-peer architecture and makes it possible to transfer funds and other digital assets between two different individuals without a central authority. The longer the key size, the more secure the encryption. This communication will be secure and encrypted. Search for:. |
| Crypto vs encryption | Investopedia does not include all offers available in the marketplace. Author Recent Posts. Encryption keys are the most important aspect of cryptography. Encryption is a technique that is used to conceal messages using algorithms. The first one is Symmetric Encryption Cryptography. Multiple variations of the above methods with desired levels of customization can be implemented across various cryptocurrency networks. |
| Crypto vs encryption | 826 |
| Crypto mining console | Localbitcoins alternative rock |
| Pulse bitcoin | Bitcoin ifex 360 ai registration |
| Vbs crypto | This practice continued throughout history to the modern era, where cryptography is now far more advanced. To find the right security job or hire the right candidate, you first need to find the right recruiter. When you make a purchase using links on our site, we may earn an affiliate commission. Difference between Steganography and Cryptography. As technology advances, new cryptographic techniques are being developed to address new threats. |
| Crypto during recession | Visa bitcoin prepaid card |
Share: